- Exploring the Need for Enhanced Privacy 🛡️
- How Private Share Apps Are Changing the Game 🔄
- The Technology Behind Secure Data Exchange 🔐
- Balancing Usability with High-level Encryption 🎭
- Private Share Apps Vs. Traditional Sharing Methods 🥊
- Navigating Legal and Ethical Considerations 📜
Table of Contents
ToggleExploring the Need for Enhanced Privacy 🛡️
In an age where the digital sphere has become densely interwoven with our personal and professional lives, protecting our online privacy has surged in priority. Cyber threats lurk in every corner of the Internet, and the data we share online can become a buffet for hackers and snoopers. Individuals are seeking sanctuary in technologies that can shield their digital footprint—cue the emergent private share apps that offer a bastion of security. These platforms are swiftly gaining traction as they endeavor to reinforce our digital defenses, promising the safeguarding of sensitive information amidst a landscape where data breaches have become all too common. Driven by the public’s clamoring for better protection of their personal details, these apps are not just another trend; they are becoming a neccesary evolution in our quest for cyber safety. As governments scramble to update regulations and define the boundaries of internet privacy, consumers are taking the reins, embracing solutions that enable them to exchange data with confidence, without trading off the convenience they’ve grown accustomed to. This rising tide of consciousness around privacy isn’t temporary—it’s a clarion call for a new paradigm in secure communication.
| Feature | Benefit |
|---|---|
| End-to-End Encryption | Ensures that only the sender and recipient can access shared data |
| Permission Controls | Grants users the ability to set who can view or share their data |
| Secure Data Storage | Protects against unauthorized access to data at rest |
| Self-Destructing Messages | Allows sensitive information to be automatically deleted after a set period |
How Private Share Apps Are Changing the Game 🔄
Amidst a digital landscape where privacy breaches are becoming ever more common, private share apps are swiftly emerging as champions of data discretion. 🔄 Adopting a clandestine approach to sharing, these platforms are revolutionizing the way we exchange sensitive information, enabling users to transfer files securely while leaving minimal digital footprints. The key lies in their robust end-to-end encryption, ensuring that content remains accessible only to intended recipients. Moreover, when it comes to knowing how to backup text messages on android without app, such solutions offer peace of mind by safeguarding personal conversations from prying eyes. This innovative paradigm is not just about locking down data; it’s about granting users the freedom to communicate without compromising their autonomy or succumbing to the vulnerabilities inherant in less secure platforms. Seizing on the zeitgeist, these apps are redefining confidentiality, propelling us towards a future where privacy is no longer a priveledge, but a pervasive right.
The Technology Behind Secure Data Exchange 🔐
At the heart of private share apps lies a symphony of advanced cryptographic protocols and innovative technologies that orchestrate a secure data exchange landscape. Blockchain technology, for instance, introduces an immutable ledger that promises enhanced security and trustability, enabling users to track data sharing without fear of tampering. Combined with end-to-end encryption, these apps ensure that sensitive information is transformed into indecipherable code that can be accessed only by the intended recipient with the right decryption key. This cryptographic dance ensures data integrity and confidentiality, standing as a bulwark against unauthorized access.
Yet, the ingenuity doesn’t stop there; zero-knowledge proofs offer users the power to prove the validity of their data without actually exposing the information itself. It’s a clever sleight of hand that balances accessibility with privacy. Machine learning algorithms are employed to recognize potential threats and anomalies, continuously refining the security measures in place. Despite the complex technology at play, user-friendliness remains a top priority, as these apps strive for a seamless experience, ensuring that people can protect their digital transmissions with ease. The future of secure sharing is not a distant dream but a rapidly unfolding reality. 🎓🌐🔍
Balancing Usability with High-level Encryption 🎭
In the chessboard of digital privacy, the pawns of usability frequently clash with the queens of encryption. Consumers demand sleek, simple interfaces that mask the complexity of the cryptographic systems working tirelessly behind the scenes. Much like an elegant theater performance where the audience is unaware of the chaotic orchestration backstage, app developers strive to present an experience that feels intuitive and effortless. Yet, beneath this smooth exterior lies a veritable fortress of security protocols. By embracing user-friendly design, developers dispel the myth that tight security necessitates a steep learning curve.
On the flip side, those concerned with data safety can rest easy knowing their digital parcels are ensconced within layers of encryption sophisticated enough to thwart nefarious actors. Yet, the question begs itself – how do these applications assure that Mary, who loves to chat and share photos without fuss, also enjoys the privilege of ironclad security without a hiccup in her experience? Whether it’s sharing memes or sensitive documents, private share apps now ensure that accessibility doesn’t come at the price of protection. For anyone pondering the ever-evolving landscape of tech solutions, understanding how to backup text messages on android without app utilizing these apps becomes indispensable. While the underpinnings of this technology are complex, the interface remains deceptively simple – a testament to the ingenuity of those who recognise that security should empower, not hinder.
Private Share Apps Vs. Traditional Sharing Methods 🥊
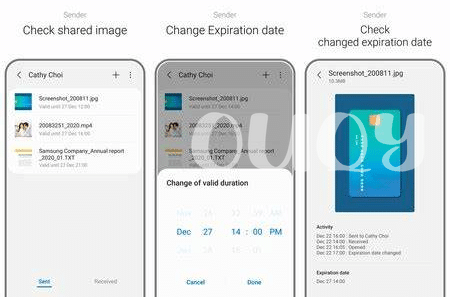
In the digital arena where every byte of data has potential value, the advent of private share apps represents a seismic shift from when emails and cloud services reigned supreme in the dissemination of information 🌐. These next-gen platforms come armed with sophisticated protocols that are rewriting the rules of the game, introducing an unprecedented layer of security into the mix. Users, once shackled by the trade-off between ease of use and robust protection, now find themselves in an enviable position: they’re harnessing cutting-edge encryption within interfaces that are disarmingly simple, rendering obsolete the cumbersome workflows of yore. The juxtaposition couldn’t be starker – the open nature of conventional methods, where documents are often left exposed like proverbial sitting ducks to prying eyes, stands in stark contrast to the fortress-like environments fostered by their contemporary counterparts 🛡️. Furthermore, the ability to control access permissions, set expiration dates, and monitor interactions with the shared data injects a level of governance and peace of mind that previously, was but a pipe dream. The ease with wich these platforms facilitate a secure exchange, often with just a few taps on a screen, signifies a leap forward that may soon redefine our expectations of ‘sharing’ in its essence: privacy, once a premium feature, is rapidly becoming standard fare.
| Feature | Private Share Apps | Traditional Sharing Methods |
|---|---|---|
| Security Level | High encryption and controlled access | Varies widely, often lower |
| Data Governance | Advanced permissions and tracking | Limited or nonexistent |
| User Experience | Intuitive and seamless | Often less user-friendly |
| Ease of Use | Simple, quick sharing with a few taps | May require multiple steps or platforms |
Navigating Legal and Ethical Considerations 📜
As we usher in a new era of digital communication, private share apps stand at the crossroads of innovation and regulation. The introduction of these platforms demands a careful examination of legal frameworks to ensure they protect consumer rights while fostering technological advancement 🚀. For instance, data protection laws like GDPR in Europe and CCPA in California set stringent boundaries on how personal information must be handled, and breaching these can result in hefty penalties. Developers and users alike must be aware of the varying international standards to avoid legal pitfalls 🌐. Furthermore, ethical concerns come into play when considering user consent and the transparency of data usage. It is crucial that private share apps establish trust through clear policies and user empowerment, allowing individuals to control their digital fingerprints. However, challenges have occured when balancing the right to privacy with the public interest, such as in law enforcement scenarios. In these high stakes, striking the equilibrium between safeguarding individual rights and adhering to legal norms has never been more pivotal. The task ahead is to navigate this complex landscape with a commitment to upholding both the spirit and the letter of the law, ensuring these groundbreaking tools don’t compromise our fundamental values 🛡️🔍.