- Unmasking Malware: the Sneaky Invaders 🕵️
- The Hall of Shame: Worst Offenders Unveiled 👾
- The Trojan Horse: Apps That Betray You 🐴
- Guard Your Gates: Security Apps You Need 🛡️
- Update or Outdate: the Key to Protection 🔄
- Safe Downloads: Spotting and Avoiding Traps 🚫
Table of Contents
ToggleUnmasking Malware: the Sneaky Invaders 🕵️
Imagine opening your phone to a new message—exciting, right? But hidden within some apps, there’s a digital pest waiting to cause havoc. These pesky programs disguise themselves so well, you might invite them in without a second thought. Just like a Trojan horse, these invaders sneak past your defenses and settle inside your device. Be wary; even the most innocent-looking game or utility app could be a front for cryptojacking, sadly turning your smartphone into a treasure trove for hackers mining cryptocurrencies without your say-so.
So, how do you keep these uninvited guests out? Well, imagine having ‘diamond hands’ with your personal information, holding on to it through thick and thin. To uphold this resilience, one must become adept at distinguishing a genuine app from a villain in disguise. Ultimately, the golden rule is DYOR—doing your research could save you from becoming an unwitting bagholder of compromised data. Stay alert and tread carefully; after all, with your data at stake, there’s no room for ‘weak hands’.
| Malware Type | Description |
|---|---|
| Cryptojacking | Unauthorized use of your phone to mine cryptocurrency. |
| Trojan Horse Apps | Seemingly harmless apps that exploit your device and data. |
| Spyware | Software that spies on your activity and steals sensitive information. |
The Hall of Shame: Worst Offenders Unveiled 👾
Picture this: You’ve just downloaded a new app, thinking it’s going to make your life so much easier, only to find out it’s got a hidden agenda. This app, a wolf in sheep’s clothing, is actually malware – an unwanted piece of software designed to harm your phone or steal your personal information. 😬 Such apps can sneak their way into your Android device, turning you into an unsuspecting bagholder of a digital headache. It’s like finding a Trojan horse at your digital doorstep, except instead of Greek soldiers, it’s full of digital mischief.
And who are these high-tech tricksters? The list changes frequently as new malware emerges and outdated threats diminish, but it’s the role of industry watchdogs to spotlight these digital delinquents. Security researchers tirelessly uncover these malicious apps and push them into the limelight, a proverbial “Hall of Shame”. It’s a round-the-clock battle against cyber villains, but you can join the fray by arming yourself with knowledge – and just a touch of crypto-slang wisdom. Remember, in the rush to get the latest useful tools, like that nifty app to mirror your phone screen to a larger display, always DYOR to avoid those sneaky traps. So next time you’re looking to splurge on new apps, perhaps for screen mirroring solutions for your Android, take a moment to consider whether it’s safe or merely a shimmering set-up for FOMO-induced regret. To find trustworthy options, you can check out a list of safe applications [here](https://androiduknewsetc.com/transform-your-device-best-android-apps-for-screen-mirroring). 🚫📲
The Trojan Horse: Apps That Betray You 🐴
Imagine downloading what seems like a helpful app, only to discover it’s secretly working against you. These apps pose as legitimate tools—games, utilities, or even antivirus software—but they’re actually wolves in digital clothing. Once installed, they may steal your personal information, snoop on your messages, or use your phone without you knowing. It’s like being a bagholder, stuck with something you thought would be valuable, but instead, it’s causing you harm.
To keep your Android safe, it’s crucial to have a defense strategy. First, always check app reviews and download counts before installing—don’t let FOMO make you an easy target. Be wary of apps that ask for too many permissions or seem too good to be true. And yes, sometimes popular apps get infected with malware through updates, so always keep an eagle eye on what your apps are up to. Think of your personal information as your most precious currency; don’t let shady apps trick you into giving it away. With a bit of caution and regular check-ups, you can avoid the latest digital Trojan horses and keep your virtual world secure. 🛠️🔐🚨
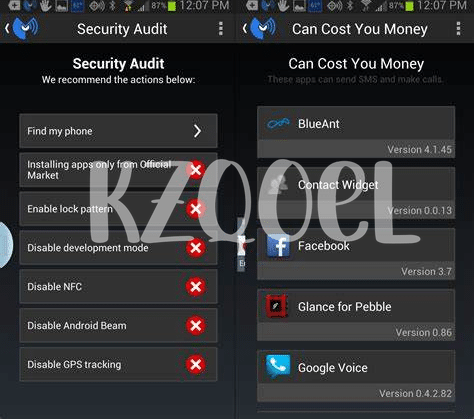
Guard Your Gates: Security Apps You Need 🛡️
Imagine your phone is like a castle, and just like any castle, it needs strong defenses to keep out unwelcome visitors. Malware apps are like crafty invaders, looking for any crack to slip through and cause mischief. But there are brave guardians out there – security apps – ready to stand watch and protect your digital kingdom. These apps act like vigilant sentries, scanning every newcomer app to ensure it’s not a Trojan Horse in disguise, waiting to betray your trust. By having a solid security app installed, you arm yourself with a loyal knight that fights off these digital dragons day and night.
But remember, just like a castle needs more than just a knight to stay safe, your phone needs more than just any security app. You need the right tools for the job. Whether it’s keeping your personal information safe from cryptojacking or helping you steer clear of that too-good-to-be-true game that’s actually a pump-and-dump scheme in disguise, an effective security app is essential. And while you’re strengthening your phone’s safety, don’t forget to enhance its functionality, too. For instance, if you’re curious about what is the best android app to mirror your phone screen, this article can point you in the right direction. Stay savvy, and keep your digital fortress secure with the right guardians at your gates.
Update or Outdate: the Key to Protection 🔄
Imagine a bustling city where bridges are crumbling but nobody bothers to fix them. That’s kind of what happens when you don’t keep your phone’s software up to date. Your digital world needs strong defenses, or else you’re skating on thin ice, and might just fall through into a world of trouble. Regular updates patch up those cracks in your online bridge, keeping the sneaky malware at bay. 🔄 Think of updates as your personal handyman, swooping in to fix leaks and reinforce walls. Updates come with the latest tricks to fend off those clever hackers and their bag of tricks. Now, it might seem a pain to stop what you’re doing and hit “update,” but it’s like choosing between a quick pit stop or a complete engine failure down the road. 🛠️
Not convinced? Let me paint a picture. The bright side of updating is like having diamond hands in the world of crypto; you’re holding on for the good stuff, security and peace of mind. On the flip side, neglecting updates? That’s FOMO you don’t want—missing out on crucial protection that could save your digital life. So before you go mooning over the latest app, remember: a simple click on “update” could be the hero move of your day. Safe and sound is the goal; outdated is just a roll of the dice. 🎲
In the world of protection, to “BTD” on your updates means grabbing that protection when it’s offered – don’t wait for the dip in security to happen. So gear up, set your phone to auto-update, and be the hero in your own digital story.
| Action | Benefit |
|---|---|
| Regular Updates | Patches security holes, blocks malware |
| Auto-Update Settings | Ensures timely updates without manual effort |
Safe Downloads: Spotting and Avoiding Traps 🚫
Ever found yourself tempted by an app that seems too cool to be true? 🤔 Protecting your phone from dodgy downloads isn’t just savvy—it’s crucial. Imagine a bazaar bustling with booths, each one luring you with flashy signs; that’s your app store. But not everything that glitters is gold. Some apps are like a wolf in sheep’s clothing 🐺, pretending to be harmless while plotting to swipe your digital coins and spill your secrets. You’ve got to be sharper than a bagholder who’s seen too many pumps and dumps, keeping a cool head to spot those tricksy traps.
Here’s a little trick to keep up your sleeve: FOMO is your enemy. That rush to download the newest app can lead to a quick regret when it’s a nasty Trojan. Always DYOR (do your own research) just like a cautious crypto investor scoping out the next big thing. Check the reviews, but not just the stars—dive into those comments. If there’s a chorus of dissatisfaction or worse, allegations of misbehavior, steer clear.
Don’t just tap “install” on a whim. Look at the permissions the app is asking for—does a wallpaper really need access to your contacts and camera? Seems fishy, right? 🎣 Keep an eye out for permission overreach. Like a trusted guard, your intuition should buzz when things don’t line up. Remember, in the world where a single tap can compromise your data, being a normie isn’t an option. Equip yourself with knowledge, suspicion, and a healthy dose of skepticism, and you’ll navigate this minefield with ease.